Master Cisco 300-740 Exam with Reliable Practice Questions
Which mitigation technique does a web application firewall use to protect a web server against DDoS attacks?
Correct : D
Start a Discussions
Which SAFE component logically arranges the security capabilities into blueprints?
Correct : A
Start a Discussions
Refer to the exhibit.
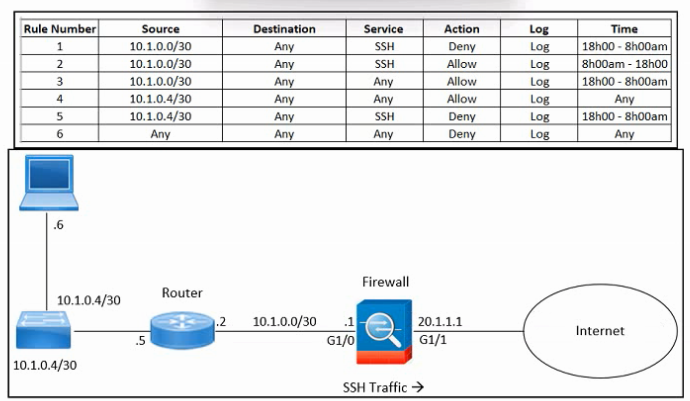
Refer to the exhibit. An engineer must troubleshoot an issue with excessive SSH traffic leaving the internal network between the hours of 18:00 and 08:00. The engineer applies a policy to the Cisco ASA firewall to block outbound SSH during the indicated hours; however, the issue persists. What should be done to meet the requirement?
Correct : B
Start a Discussions
Refer to the exhibit.
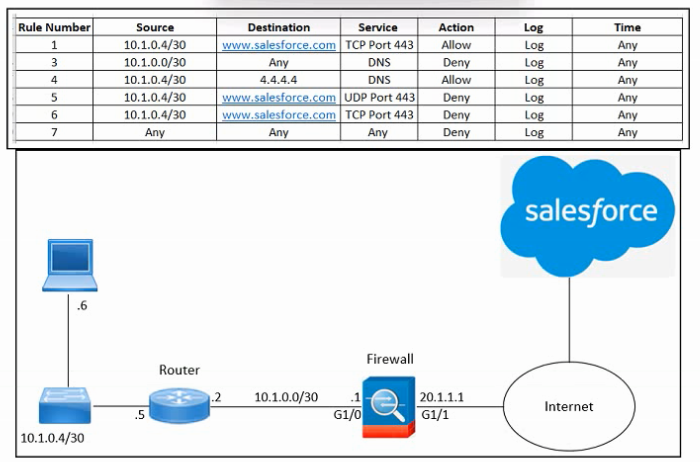
Refer to the exhibit. An engineer must configure the Cisco ASA firewall to allow the client with IP address 10.1.0.6 to access the Salesforce login page at https://www.salesforce.com. The indicated configuration was applied to the firewall and public DNS 4.4.4.4 is used for name resolution; however, the client still cannot access the URL. What should be done to meet the requirements?
Correct : A
Start a Discussions
An engineer is configuring multifactor authentication using Duo. The implementation must use Duo Authentication Proxy and the Active Directory as an identity source. The company uses Azure and a local Active Directory. Which configuration is needed to meet the requirement?
Correct : D
Start a Discussions