Master Fortinet FCSS_EFW_AD-7.6 Exam with Reliable Practice Questions
Refer to the exhibit.
A pre-run CLI template that is used in zero-touch provisioning (ZTP) and low-touch provisioning (LTP) with FortiManager is shown.
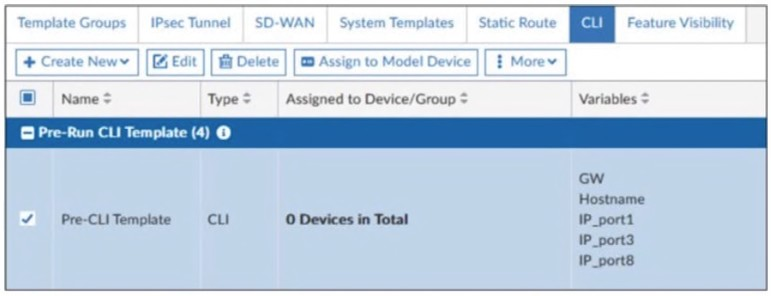
The template is not assigned even though the configuration has already been installed on FortiGate.
What is true about this scenario?
Correct : B
In FortiManager, pre-run CLI templates are used in Zero-Touch Provisioning (ZTP) and Low-Touch Provisioning (LTP) to configure a FortiGate device before it is fully managed by FortiManager.
These templates apply configurations when a device is initially provisioned. Once the pre-run CLI template is executed, FortiManager automatically unassigns it from the device because it is not meant to persist like other policy configurations. This prevents conflicts and ensures that the FortiGate configuration is not repeatedly applied after the initial setup.
Start a Discussions
An administrator needs to install an IPS profile without triggering false positives that can impact applications and cause problems with the user's normal traffic flow.
Which action can the administrator take to prevent false positives on IPS analysis?
Correct : A
False positives in Intrusion Prevention System (IPS) analysis can disrupt legitimate traffic and negatively impact user experience. To reduce false positives while maintaining security, administrators can:
Use IPS profile extensions to fine-tune the settings based on the organization's environment.
Select the correct operating system, protocol, and application types to ensure that IPS signatures match the network's actual traffic patterns, reducing false positives.
Customize signature selection based on the network's specific services, filtering out unnecessary or irrelevant signatures.
Start a Discussions
An administrator is setting up an ADVPN configuration and wants to ensure that peer IDs are not exposed during VPN establishment.
Which protocol can the administrator use to enhance security?
Correct : A
In ADVPN (Auto-Discovery VPN) configurations, security concerns include protecting peer IDs during VPN establishment. Peer IDs are exchanged in the IKE (Internet Key Exchange) negotiation phase, and their exposure could lead to privacy risks or targeted attacks.
IKEv2 encrypts peer IDs, making it more secure compared to IKEv1, where peer IDs can be exposed in plaintext in aggressive mode.
IKEv2 also provides better performance and flexibility while supporting dynamic tunnel establishment in ADVPN.
Start a Discussions
Refer to the exhibit, which shows an enterprise network connected to an internet service provider.
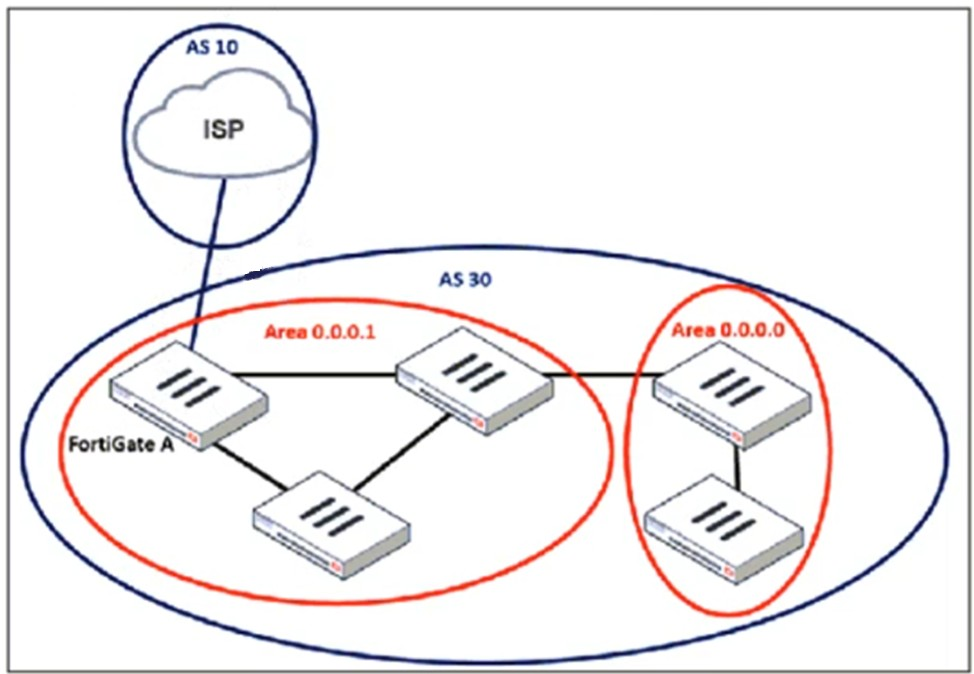
An administrator must configure a loopback as a BGP source to connect to the ISP.
Which two commands are required to establish the connection? (Choose two.)
Correct : A, B
When configuring a loopback interface as the BGP source for connecting to an ISP, two important settings must be applied:
1. Enable EBGP Multihop (ebgp-enforce-multihop)
2. Set the Update Source (update-source)
Start a Discussions
The IT department discovered during the last network migration that all zero phase selectors in phase 2 IPsec configurations impacted network operations.
What are two valid approaches to prevent this during future migrations? (Choose two.)
Correct : A, C
Zero phase selectors in IPsec Phase 2 mean that no specific traffic selectors (subnets) are defined, allowing any traffic to be encrypted through the VPN tunnel. This can cause unintended traffic forwarding issues and disrupt network operations.
To prevent this from happening during future migrations:
Using routing protocols ensures that only specific subnets are advertised over the tunnel. Dynamic routing (such as OSPF or BGP) helps define which networks should use the tunnel, preventing unintended traffic from being encrypted.
Clearly defining phase 2 selectors avoids the problem of encrypting all traffic by explicitly stating the allowed source and destination subnets. This prevents the tunnel from affecting unrelated network traffic.
Start a Discussions